Today, drones are just as likely to deliver packages as they are to disrupt critical infrastructure or military operations. As the need for robust, adaptable counter-drone solutions becomes increasingly apparent, D-Fend Solutions, the leading company in RF-cyber takeover technology, sets the standard for multi-layered drone defense. In an exclusive interview on the recent Dawn of Autonomy podcast, Gordon Kesting, D-Fend’s Vice President of U.S. Sales & Business Development, discussed the evolving drone threat, the need for defense-in-depth to combat it, and how his company’s battle-proven RF-cyber technology provides the cornerstone for holistic and integrated airspace awareness and protection, in any context.
Gordon Kesting: Engineering Expertise Meets Security Strategy
Kesting’s deep experience in national defense and homeland security is rooted in decades of technical leadership. With multiple engineering degrees, his early career focused on designing radars and cockpit systems for fighter aircraft, as well as flight controls for both military and commercial aviation. He later expanded into C4 (Command, Control, Communications, and Computers) applications for defense and border security. Now, as VP of Sales & Business Development for D-Fend Solutions’ North America operations, Kesting applies this technical rigor and strategic vision to the fight against unmanned aerial threats across military, homeland security and commercial sectors because, in his words, “the drone threat is everywhere.”
The Evolving Threat: Why RF-Cyber Matters Now
The proliferation of drones—commercial, do-it-yourself (DIY), and military-grade—has transformed the airspace into a contested domain. Recent headlines underscore the urgency of the situation. President Trump’s recent Executive Order (EO) on airspace sovereignty and Operation Spider’s Web and in the Russo-Ukraine conflict, both launched this month, underscore the growing sophistication and frequency of drone threats.
Real-World Conflict: Operation Spider’s Web
On the battlefield, drones have become force multipliers and asymmetric threats. On June 1, Ukraine kicked off its meticulously planned mission, Operation Spider’s Web. Ukrainian operatives covertly smuggled 117 small attack drones into Russia, hiding them in modified trucks with remotely operated roofs. These drones were then launched near five strategic airbases and targeted Russia’s long-range bombers and surveillance aircraft across thousands of kilometers and inflicting up to $7 billion in losses. Ukrainian officials claim 41 aircraft were damaged or destroyed, including a significant portion of Russia’s strategic bomber fleet, many loaded with cruise missiles.
According to Kesting, this attack demonstrated how low-cost, commercially available drones—some guided by open-source software and AI-assisted targeting—can deliver precision strikes deep behind enemy lines. He also noted that this unprecedented operation further highlights the urgent need for effective, multi-layered counter-drone defenses to protect high-value assets from such evolving threats.
“We continue to see the strategic significance of using group one and group two—these small UAS—particularly in a creative and innovative way as they were deployed here… It just points to the ongoing need for effective countermeasures,” he said.
Policy Shifts: The Trump Executive Order
The Trump administration’s EO on airspace security acknowledges a heightened federal awareness of, and focus on, the risks posed by unmanned aircraft systems (UAS). Kesting observed, “It’s interesting that the president and his administration are taking this kind of notice of drones, both UAS as well as the drone threat… They specifically call out things like the upcoming World Cup as well as the Olympics.”
Indeed, the order specifically addresses threats to such mass gatherings. It calls for grants to state, local, tribal, and territorial (SLTT) agencies to acquire both UAS and counter-UAS technologies and acknowledges the need to update federal laws to keep pace with rapid technological change in both the drone and counter-drone sectors.
The Problem: Drones as Dual-Use Tools
Drones are not inherently malicious; they serve countless beneficial purposes in agriculture, logistics and emergency response. However, their accessibility and adaptability make them attractive force multipliers and asymmetric threats, for activities ranging from surveillance and espionage to direct attacks.
Kesting elaborated on the challenge presented when bad actors use commercial drones for nefarious purposes. “We’re particularly focused on the smaller group one, group two, some group three drones, as they are transforming the landscape…” he said. “Particularly widely used commercial drones, as well as DIY drones that are quite easily built up from components you can buy online.”
With 80% of critical infrastructure in the U.S. privately owned, relying solely on government response is impractical. The need for scalable, effective countermeasures that can be deployed across diverse environments—airports, borders, stadiums, and power plants—has become clear.
RF-Cyber Technology: The Cornerstone of Defense in Depth
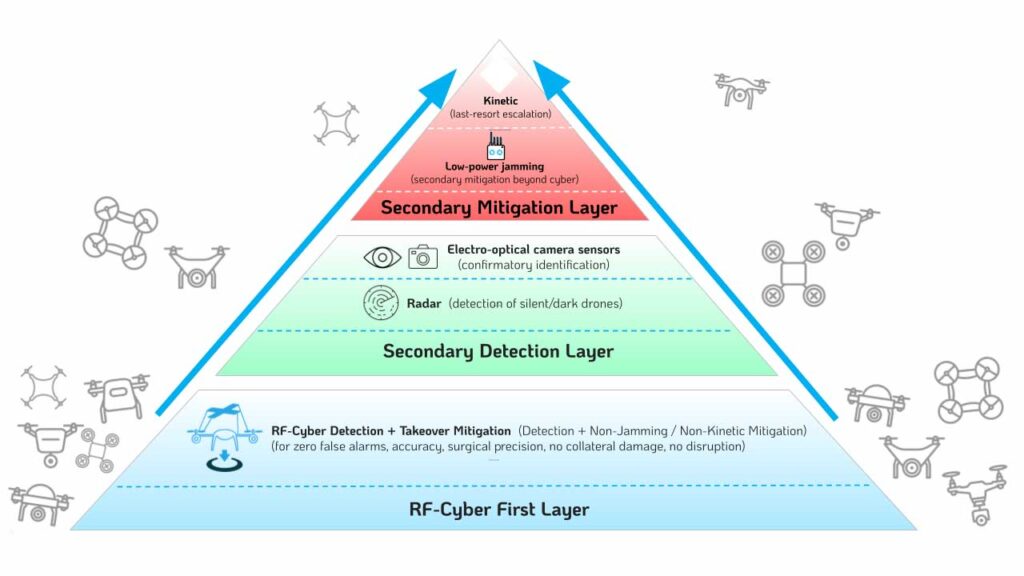
The consensus among security professionals is equally clear: there is “no silver bullet” (Kesting’s words) for counter-drone defense. Instead, professionals build the most resilient architectures in a layered, defense-in-depth approach. RF-cyber takeover technology, as exemplified by D-Fend Solutions’ EnforceAir, serves as the ideal foundation for such systems, Kesting explained.
What Is RF-Cyber Takeover?
RF-cyber takeover leverages radio frequency (RF) signals to detect, identify, track, and assume control of rogue drones. Unlike jamming, which indiscriminately disrupts all signals in an area, RF-cyber’s precise methods allow defenders to safely land or redirect drones to predesignated locations without collateral damage.
This approach is especially valuable in sensitive environments—urban centers, airports, and military bases—where indiscriminate jamming or kinetic interventions could endanger people or critical systems.
“We are enabling full control, safety and continuity of operations as we detect, track and identify drones… including a safe takeover, where we’re then landing them in a safe designated spot that we’ve already predetermined, or sending it back to the operator or takeoff position,” Kesting noted.
Why Start with RF-Cyber?
RF-cyber provides a foundational layer as defenders start to build multilayered systems. It provides both the sensing element to do the detection, tracking, and identification as well as a mitigation element to control the drone and mitigate or defeat it.
According to Kesting, RF-cyber solutions offer several key advantages:
- Dual Functionality: RF-cyber addresses the entire drone life cycle by providing detection, tracking, identification to and mitigation AND defeat capabilities in a single layer.
- Cost-Effectiveness and Coverage: Drone incursions in most environments will likely come from commercial and DIY drones that operate on RF protocols known by the system. Therefore, RF-cyber systems can address a high percentage of threats “out of the box.” D-Fend Solutions continually updates its protocol knowledge base to stay ahead of emerging platforms.
- Passive Detection and Low Power Mitigation: By listening rather than emitting to detect, track and identify drones, RF-cyber systems reduce vulnerability of being “seen” by adversaries in the electromagnetic spectrum, particularly in military settings where it is important to remain stealthy. Furthermore, mitigation uses very low power RF for a short period of time and thereby avoids interfering with friendly communications or causing vulnerabilities associated with being detected.
- Low Physical Collateral Impact: Unlike kinetic or high-powered jamming solutions, RF-cyber methods minimize unintended consequences of falling projectiles or debris. This makes them suitable for densely populated or critical infrastructure environments.
No Silver Bullet: The Case for Layered Defense
RF-cyber remains foundational within a layered indispensable approach. Integrating RF-cyber with radar, optical sensors, and even kinetic or directed-energy countermeasures creates a holistic defense system that compensates for the limitations of any single technology.
Kesting elaborated, “There’s a general acknowledgement across the whole community that in order to address the entire spectrum of threats and missions… there’s going to be a need for many different technologies to be integrated into what we can call this multi-layer approach.”
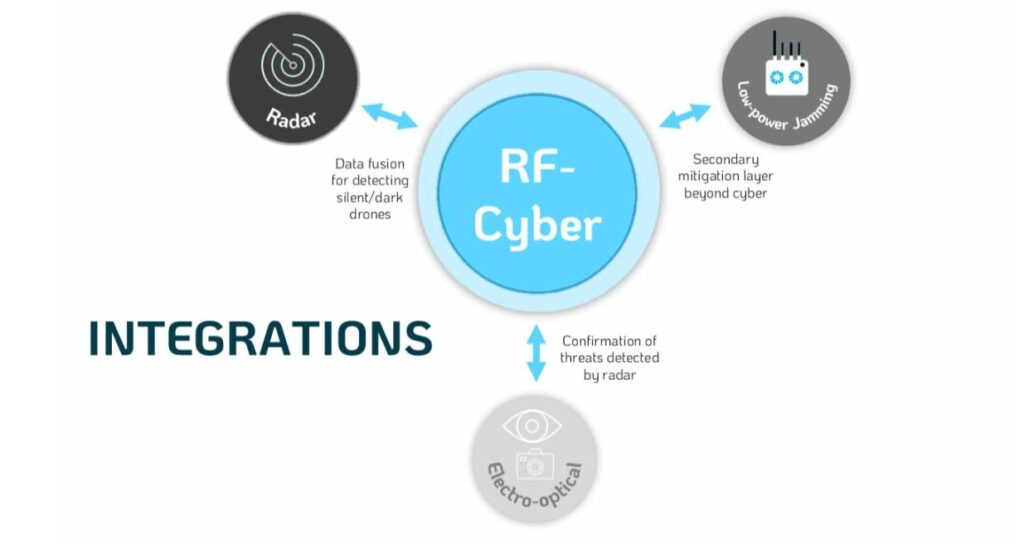
Integration in Practice: EnforceAir as a Foundation
D-Fend Solutions designed its EnforceAir system to seamlessly integrate with other complementary counter-UAS technologies. For instance, while radar provides active detection——RF-cyber offers a no-false-alarm baseline and precise mitigation. Cameras can be cued to locations identified by RF-cyber detection to provide visual confirmation and evidentiary support for law enforcement or military action.
Kesting said one would start with RF-cyber as the foundational layer for reasons discussed earlier. “The next layer might be radar to build in a detection sensor for otherwise undetectable drones. Next could be a camera, which our cyber system can cue to get ‘eyes on’ the drone and its payload since we provide accurate location information for the drone, the pilot/controller, and the home point of the drone,” he said. Finally, a low power jammer can be incorporated as an adjunct defeat mechanism with the RF-cyber.
As these multi-layered systems are built up, integration becomes a key. Effective integration will allow the sensors and effectors to be used together in the most effective combination for the threat at hand.
Real-World Validation: Combined Resolve 25-02
The effectiveness of EnforceAir and the layered defense concept was put to the test at the recent Combined Resolve 25-02, a major U.S. Army-led exercise at the Joint Multinational Readiness Center in Hohenfels, Germany. There, Kesting, and some of his D-Fend Solutions colleagues worked directly with soldiers, training them to deploy EnforceAir in vehicle, tripod, and backpack configurations. The system’s portability and ease of use allowed it to be employed at various echelons, from infantry squads to brigade headquarters.
The exercise not only validated the technology in realistic field conditions but also demonstrated the value of rapid commercial technology adoption in military contexts. Soldiers quickly learned to operate the system, and its modularity allowed for flexible deployment across different operational needs.
The Future of RF-Cyber and D-Fend Solutions
As drone technology continues to evolve—and as regulatory frameworks like the anticipated beyond visual line of sight (BVLOS) Part 108 rule take shape—D-Fend Solutions remains committed to staying ahead of the curve. The company continues to focus on expanding its protocol and threats knowledge base, participating in key industry and defense events to develop industry connections, and deepening integration with other counter-UAS technologies.
On this last point, Kesting elaborated, “We’re going to keep tracking the rapidly evolving drone counter-drone world and…leverage our RF-cyber as the foundational layer…building up more complete counter-drone solutions.”
D-Fend’s commitment extends beyond technology. The company maintains a comprehensive, publicly accessible situational awareness tool for policymakers, infrastructure owners, and the general public. As the threat landscape shifts, D-Fend Solutions stands poised to adapt and ensure that RF-cyber remains the bedrock of multi-layered drone defense worldwide.
Building Resilience, One Layer at a Time
The rise of drones as both tools and threats demands a nuanced, adaptable approach to security. D-Fend Solutions’ RF-cyber takeover technology, embodied in its EnforceAir system, offers a proven, scalable foundation for multi-layered defense. By integrating seamlessly with radar, optical, and jamming and kinetic solutions, D-Fend enables end users—from military commanders to critical infrastructure operators—to build resilient, context-sensitive defenses against the full spectrum of drone threats.
As Kesting and his team continue to innovate and collaborate, the message is clear: in the world of counter-drone defense, it’s not about finding a silver bullet—it’s about building a better shield, layer by layer on the right foundation.
By: Dawn Zoldi

